Palo Alto Unit 42 Uncovers Slow Pisces Attack on Crypto Developers
Palo Alto Unit 42 has reported on the recent Slow Pisces attack targeting cryptocurrency developers via LinkedIn. The threat actors impersonated potential employers and distributed malware disguised as coding challenges. As a result, developers unwittingly ran compromised projects infecting their systems with RN Loader and RN Stealer.
The report identified a total of 54 indicators of compromise (IoCs), which included 27 domains and 27 IP addresses. Further analysis uncovered the following interconnected artifacts:
- 12 alleged victim IP records linked to five Autonomous System numbers (ASNs)
- 551 email-connected domains
- One additional malicious IP address
- 179 IP-connected domains
- 389 string-connected domains, of which three were found to be malicious
For those interested, a sample of the analyzed artifacts can be downloaded from the official website.
A Closer Examination of Slow Pisces IoCs
The investigation into the 54 IoCs identified by Palo Alto Unit 42 commenced with a detailed analysis.
Initial inquiries using the Bulk WHOIS API revealed that out of the 27 IoC domains, only 26 had up-to-date WHOIS records. Key findings included:
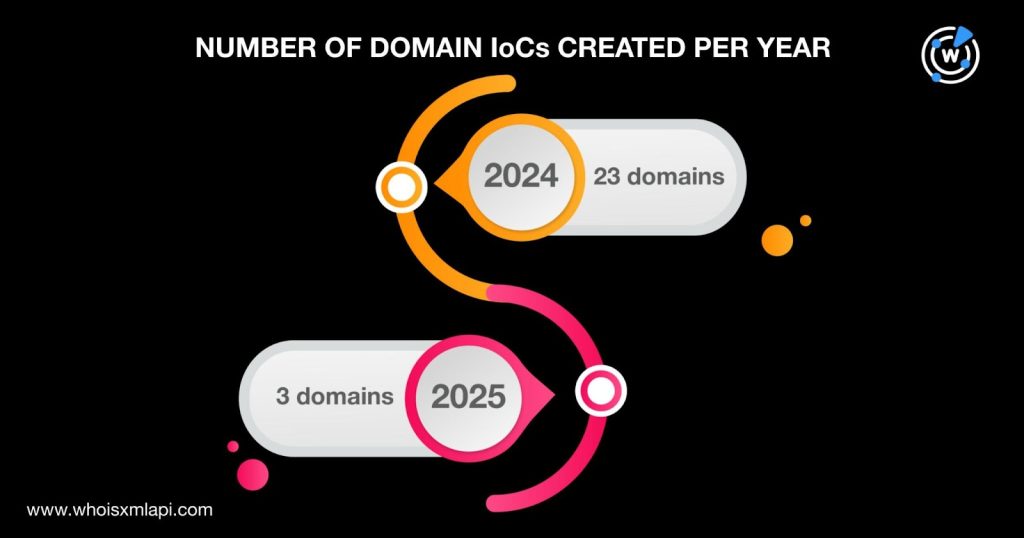
- All 26 domains with current WHOIS records were registered between 2024 and 2025, predominantly in Iceland under Namecheap administration.
-
While one domain lacked a registrant country, the remaining 25 were split between Iceland and the U.S.
Subsequent queries via the DNS Chronicle API found that 24 IoC domains had historical domain-to-IP address resolutions, with the domain leaguehub[.]net boasting the earliest resolution date of February 6, 2017.
Expansion of IP Address Analysis
Further investigations utilizing Bulk IP Geolocation Lookup disclosed that the 27 IoC IP addresses were distributed across 12 countries. The top countries included the Netherlands with the highest count, followed by France, Poland, and the U.K.
Notably, additional scrutiny revealed the ISPs responsible for the IP addresses’ administration, shedding light on potential sources of these malicious activities.
This summary provides a glimpse into the comprehensive research carried out. For full details and artifact samples, please visit our site.